
Kuika's Verify Recaptcha Token action is used to enhance security measures in your application. By checking the token obtained from the user's reCAPTCHA verification, it helps you verify that the person performing the action is a real user. This action allows you to filter out spam, bot, or malicious software-generated requests.
For this action to work correctly, Google reCAPTCHA key information must be defined in the system via the Configuration Manager module. For example, when a user fills out a registration form and passes the reCAPTCHA verification, this action verifies the reCAPTCHA token via Google servers. If the verification is successful, the process continues; if unsuccessful, the system blocks the process to prevent malicious use.
Technical Features
Defining the Action in UI Design
Configuring Action Parameters
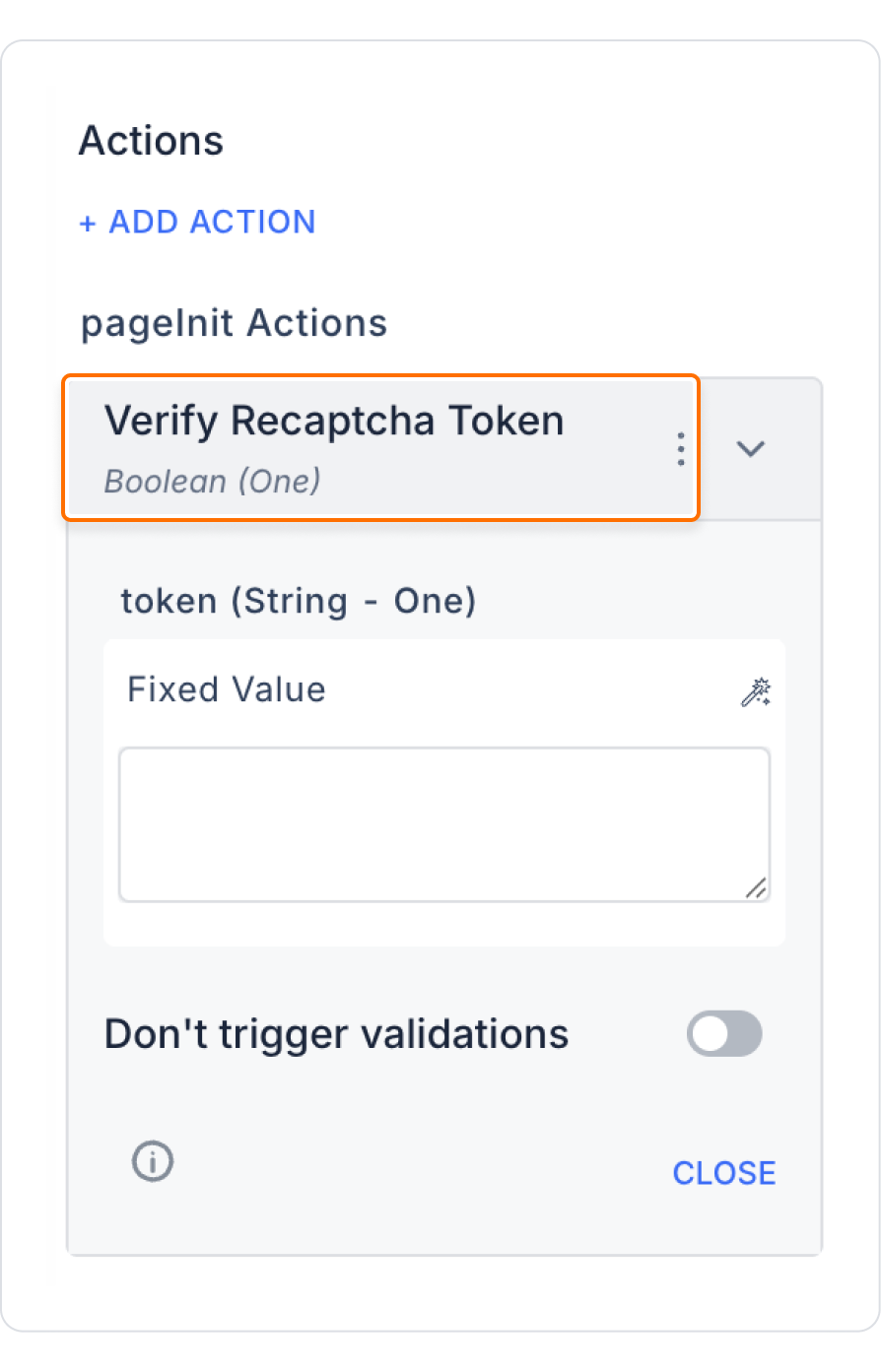
A user filling out a registration form is asked to complete a reCAPTCHA verification. When the user clicks the “Sign Up” button, the Verify Recaptcha Token action is executed first. If the token is verified, the registration process continues; otherwise, an error message is displayed.
Adding a reCAPTCHA Verification Action Before User Registration
Configuring the Verify Recaptcha Token Action
With this configuration, reCAPTCHA verification is automatically performed when the user clicks the button. If the verification is successful, the process continues; otherwise, it is stopped.
Depending on the verification result
Token values can be used appropriately with Google reCAPTCHA v2 and v3 support. Verification strategies can be applied as visible (v2) or invisible (v3) according to the form structure.
The token can be obtained in the following ways:
Technical Risks
The Verify Recaptcha Token action enhances security in your application by integrating reCAPTCHA verification. It provides a strong defense against spam and bots, allowing only real users to perform actions. With support for both web and mobile applications, it can be easily implemented in any user interaction and adapted to advanced security scenarios.
