
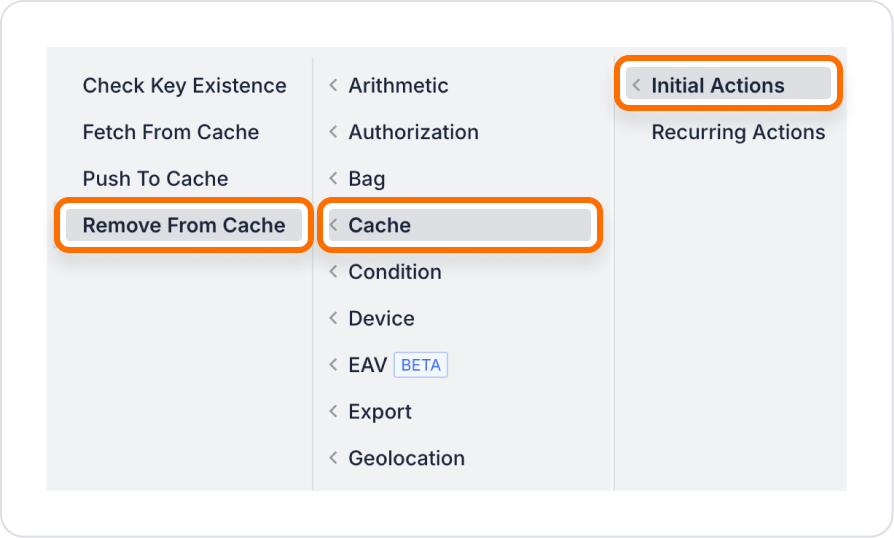
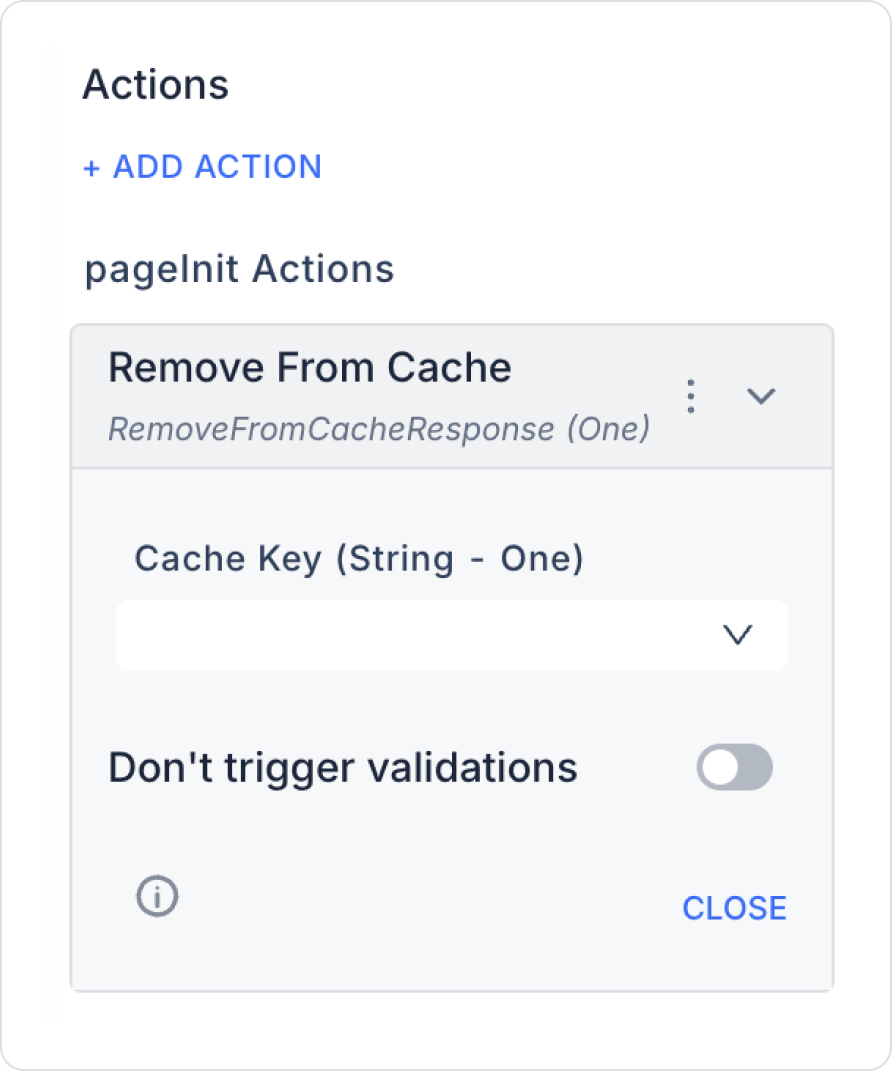
Remove From Cache allows you to delete data previously added to the cache on the Kuika platform using the specified key. If the specified key does not exist in the cache or has been previously deleted, the action returns the error “Given key does not exist.” This action allows you to clean up unnecessary or outdated data from the cache, thereby maintaining application performance and data integrity. Supported cache providers are Redis and Memory, each of which is managed through the Configuration Manager.
Important Points
Scenario: In an e-commerce application, the user has previously saved product filters with Push To Cache. However, they now want to clear the old filters. With the Remove From Cache action, these filters are deleted from the cache, and subsequent Fetch From Cache operations cannot return data from this key.
Step-by-Step Usage
Technical Risks
