
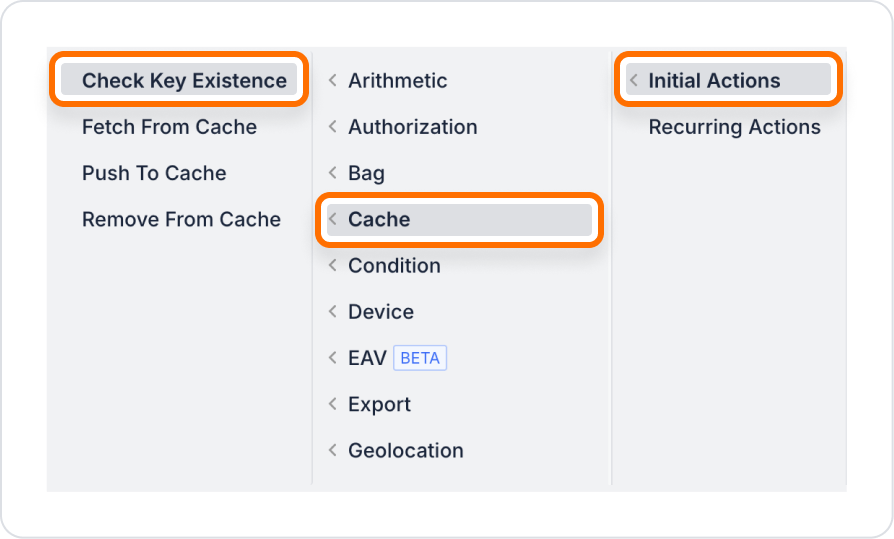
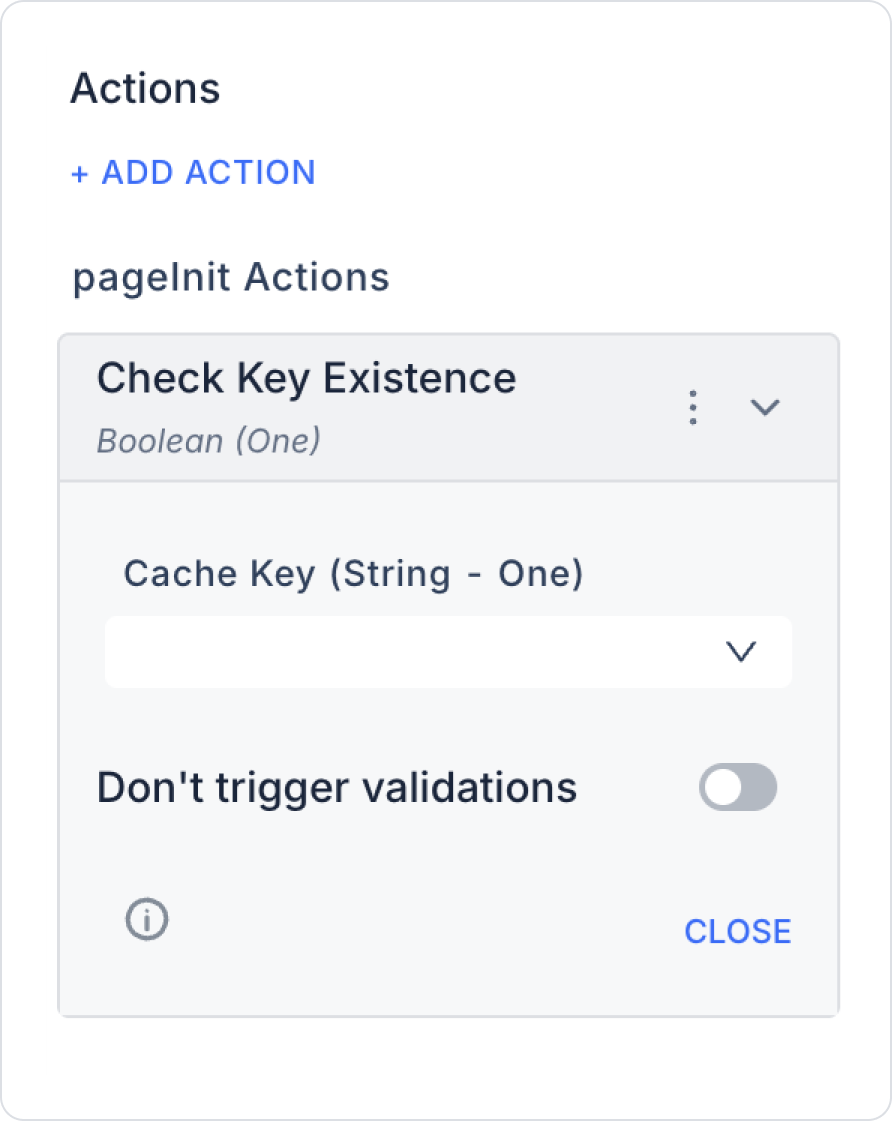
Check Key Existence allows you to check whether a cache key previously added with Push To Cache on the Kuika platform exists in the cache. This action allows you to verify the existence of dynamically added keys while the application is running and provides a secure control mechanism for subsequent actions (Fetch From Cache, Remove From Cache, etc.). Supported cache providers are Redis, Mongo, SQL, and Memory, each of which is managed through the Configuration Manager.
Important Points
In an e-commerce application, the user has saved product filters with Push To Cache. Before the user applies the filters, the Check Key Existence action checks whether the filters are in the cache. This ensures that the Fetch From Cache or Remove From Cache actions only work with valid keys.
Step-by-step usage
Technical Risks
